
Authors:


Digital payments have become the backbone of modern commerce, with millions of transactions flowing through systems like UPI every day. While this convenience has enhanced our daily lives, it has also created new opportunities for fraudsters who constantly evolve their tactics to exploit payment systems. The challenge for financial institutions is no longer just about detecting fraud - it's about doing so without compromising the lightning-fast experience users expect.
NPCI's latest breakthrough addresses this complex challenge through G-TED SAM (Graph Transformer Distillation to Simple Attention Model), an innovative framework that delivers sophisticated fraud detection capabilities while maintaining efficiency. This advancement represents a significant leap forward in protecting India's digital payment ecosystem.
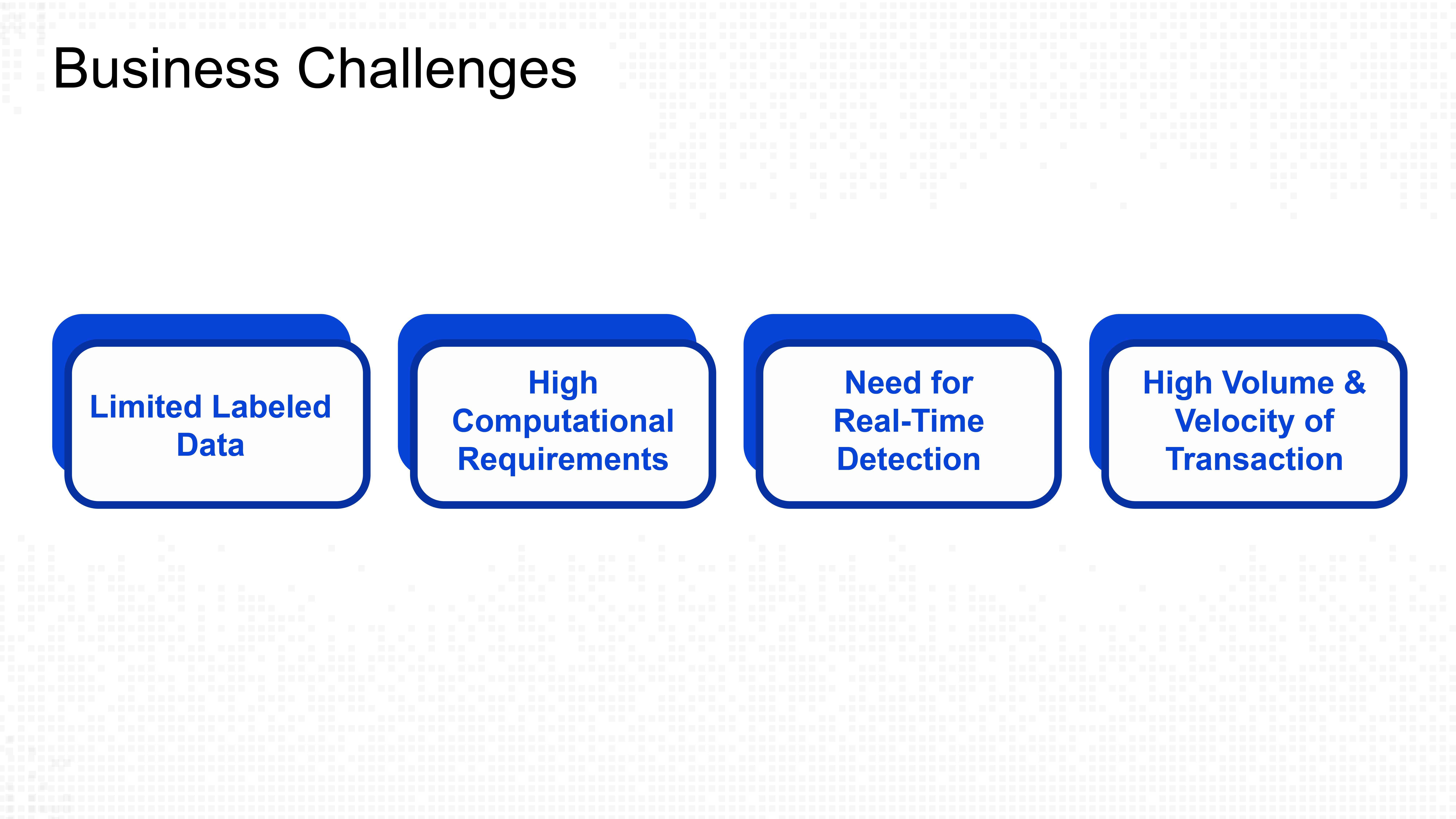
Modern financial fraud has evolved far beyond simple card skimming or stolen passwords. Fraudsters now operate sophisticated networks, creating complex webs of fake accounts and coordinated attacks that traditional rule-based systems struggle to detect.
Current Fraud Challenges:
Graph Neural Networks and Graph Transformers excel at identifying suspicious patterns by examining entity interactions within payment networks. However, their computational complexity creates bottlenecks that impact transaction processing speed.
The need for a solution maintaining analytical sophistication while delivering efficient and accurate performance led to G-TED SAM's development.
G-TED SAM employs a teacher-student knowledge distillation framework specifically designed for graph-based fraud detection. This approach allows a sophisticated model to transfer its learned insights to a more efficient model without sacrificing detection accuracy.
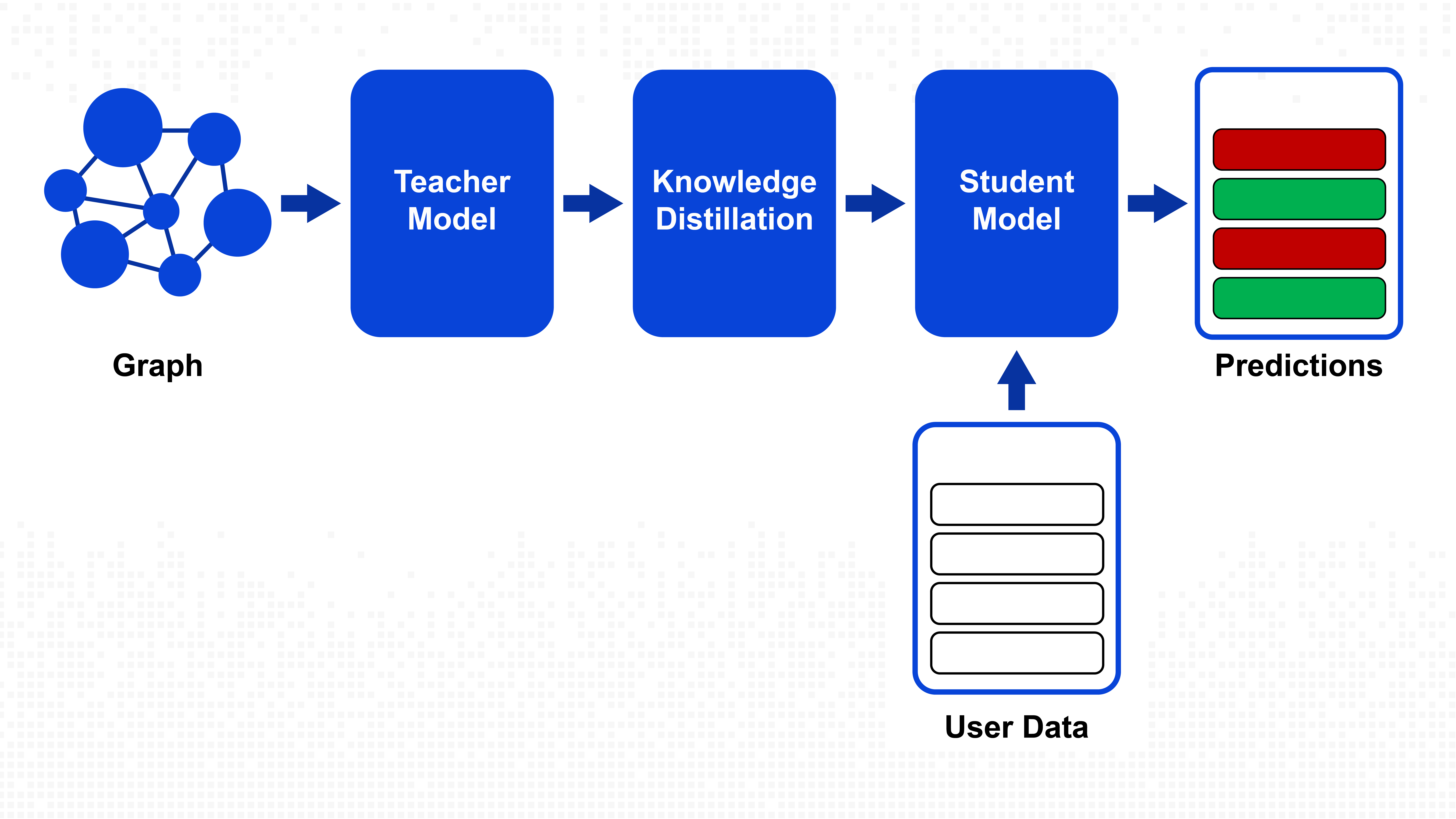
The teacher component utilises a Graph Transformer architecture that analyses the complete network of transactions and user relationships. This model understands fraud patterns by examining how different accounts interact, identifying suspicious networks and unusual transaction flows.
Teacher Model Capabilities:
The Graph Transformer's strength lies in understanding not just individual transactions but the complex web of relationships that indicate fraudulent activity.
The knowledge distillation process represents the heart of G-TED SAM's innovation. Rather than simply copying the teacher model's outputs, the framework focuses on transferring the most critical components of the teacher's decision-making process.
The teacher model's attention mechanism functions through key and query components. The query represents questions being asked by target nodes in the transaction graph, while keys provide information from neighboring nodes. This interaction allows the model to understand which relationships are most important for fraud detection.
G-TED SAM's distillation process teaches the student model to replicate these essential attention patterns without requiring access to the full graph structure. This selective knowledge transfer ensures that the student model learns meaningful fraud detection capabilities while maintaining computational efficiency.
The student model represents a streamlined architecture that can operate independently of graph structure during inference. Once trained, it detects fraud using only basic transaction information without needing to analyse the entire network.
The student model can process transactions quickly because it doesn't need to query neighboring nodes or perform complex graph traversals. Instead, it applies learned attention patterns directly to transaction features.
The student model's lightweight design makes it suitable for deployment across different hardware configurations, from high-performance server environments to resource-constrained edge computing scenarios. This flexibility is essential for organisations operating distributed payment processing systems.
Traditional fraud detection systems force organisations to choose between accuracy and speed. Complex models that can catch sophisticated fraud often introduce latency that impacts user experience, while fast models may miss subtle fraudulent patterns.
G-TED SAM eliminates this trade-off through its innovative approach to knowledge transfer. The framework enables organisations to benefit from sophisticated graph analysis without bearing the computational cost.
The student model's architecture enables processing speeds that are hundreds of times faster than traditional graph-based approaches. This performance improvement stems from several design decisions optimising the model for inference efficiency.
Key Performance Features:
These capabilities allow processing millions of transactions with minimal impact on user experience, maintaining seamless payment flows while providing robust fraud protection.
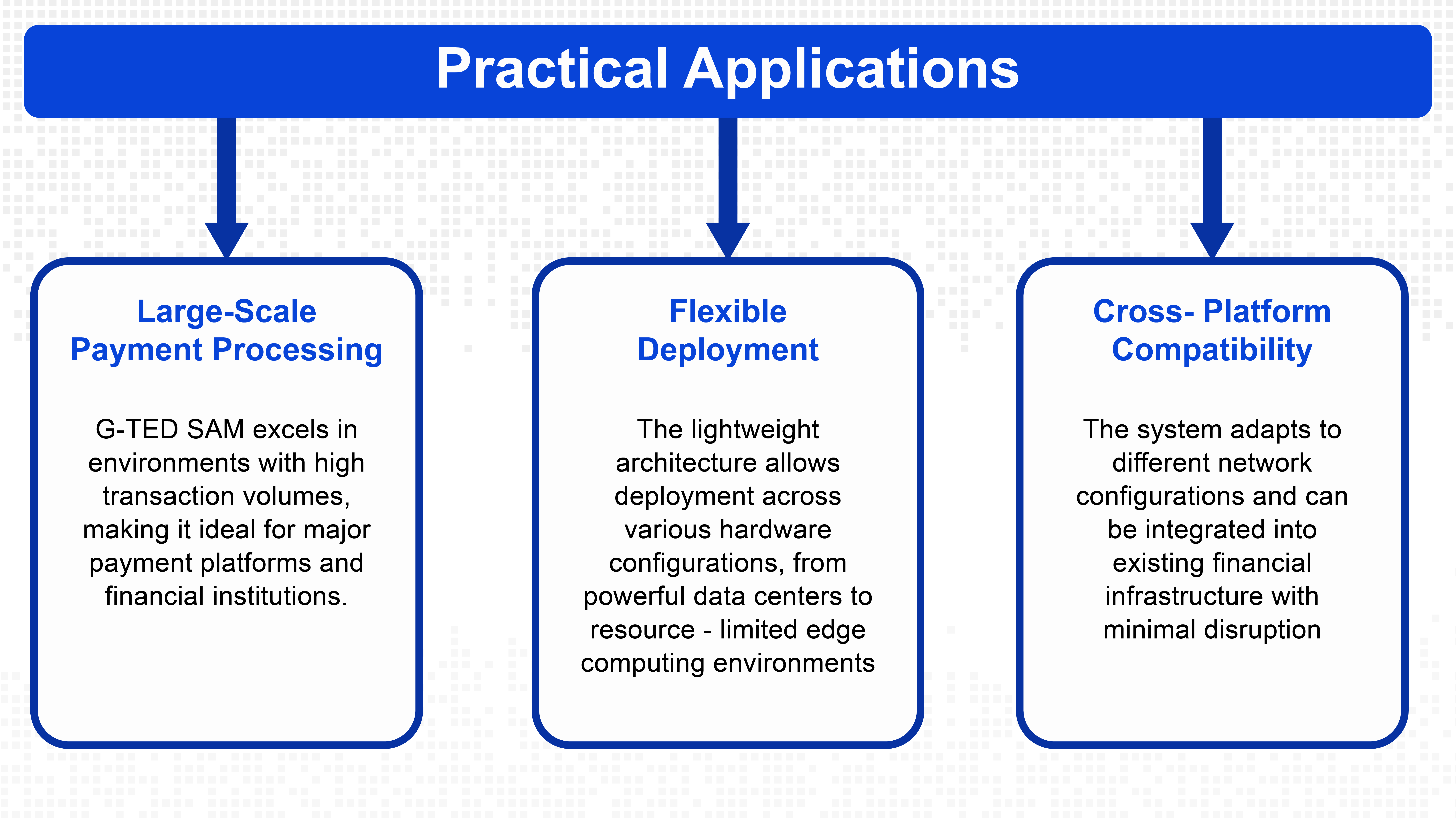
The framework's design enables deployment across various network configurations without requiring modifications to the core architecture. This scalability supports organisations operating complex payment infrastructures with different geographical and technical constraints.
The system adapts to different transaction volumes and network patterns while maintaining consistent performance, making it suitable for both large-scale national payment systems and smaller regional networks.
NPCI's evaluation of G-TED SAM utilised real UPI transaction data spanning one month, providing insights into the framework's performance under actual operating conditions.
The system significantly enhances fraud detection compared to traditional methods, catching sophisticated fraud patterns that simpler models would miss. This improvement stems from the student model's ability to apply insights learned from comprehensive graph analysis without computational overhead.
Detection Capabilities:
G-TED SAM delivers substantial operational benefits that make it practical for large-scale deployment:
Operational Benefits:
G-TED SAM maintains the seamless payment experience users expect. The system's speed ensures fraud detection doesn't introduce noticeable delays in transaction processing, preserving the convenience that has made digital payments popular.
This balance between security and user experience maintains user trust and adoption of digital payment systems.
G-TED SAM's flexible architecture makes it suitable for various deployment scenarios within the financial services industry. The framework's ability to operate without explicit graph structure during inference enables adaptation to different organisational needs and technical constraints.
The development of G-TED SAM represents a significant advancement in applying machine learning to practical financial security challenges. The framework demonstrates how academic research can be translated into solutions that address real-world operational requirements.
G-TED SAM extends knowledge distillation techniques into the domain of graph-based fraud detection, opening new possibilities for applying this approach to other network analysis challenges. The framework's success demonstrates that complex graph relationships can be effectively transferred to simpler models without significant accuracy loss.
This advancement has implications beyond fraud detection, potentially benefiting other applications that require analysis of network relationships while maintaining processing efficiency.
The framework addresses one of the fundamental challenges in deploying advanced AI systems in production environments: balancing sophistication with operational requirements. G-TED SAM demonstrates that it's possible to achieve both sophisticated analysis and practical deployment efficiency through careful architectural design.
This approach provides a model for other AI applications that face similar trade-offs between analytical capability and operational constraints.
The efficiency gains provided by G-TED SAM support financial inclusion by making advanced fraud detection accessible to organisations with limited technical resources. This capability helps ensure that sophisticated fraud protection isn't limited to large institutions with extensive computational infrastructure.
Smaller financial institutions and emerging payment providers can leverage G-TED SAM to offer secure payment services while maintaining competitive transaction processing costs.
The success of G-TED SAM opens several avenues for future development and application in financial security and beyond. The framework's approach to knowledge distillation provides a foundation for addressing other challenges that require balancing analytical sophistication with operational efficiency.
Future developments could extend G-TED SAM's approach to other types of financial fraud and security challenges. The framework's architecture could be adapted to detect money laundering, market manipulation, or other complex financial crimes that involve network analysis.
The knowledge distillation approach could also be applied to other domains where relationship analysis is important, such as cybersecurity threat detection or social network analysis.
Future versions of G-TED SAM could incorporate enhanced explainability features that help organisations demonstrate compliance with regulatory requirements for AI-based decision-making systems. This capability would be particularly valuable as financial regulators develop more sophisticated requirements for AI governance.
G-TED SAM represents more than a technical achievement—it embodies NPCI's commitment to maintaining the security and integrity of India's digital payment infrastructure. As digital payments continue growing and fraud techniques become more sophisticated, frameworks like G-TED SAM prove essential for maintaining user trust and system security.
The framework's success demonstrates that Indian institutions can develop world-class AI solutions addressing practical challenges while maintaining performance characteristics required for large-scale deployment. This achievement supports India's position as a leader in financial technology innovation and advances the country's broader digital transformation goals.